Earlier today, a Twitter account named @ligatthacker tweeted that the web site owned by Gregory D. Evans and High Tech Crime Solutions was compromised (DatalossDB entry). The tweet included a link to a Pastebin dump as a sample of the SPOOFEM sent message database. It also included a second link to a download of the entire database, 32,167 messages in total, PGP signed by RSA key ID 7F5AF73C. Each message includes the following fields: email_to, time, date, email_msg, email_subject, spoof_name, sms_to, email_your_name, sms_msg, user, and id. In short, every spoofed SMS or email message that has been sent through the service is now public. The following is an example of a message:
{"email_to":"","time":"06:36:39","date":"2012-03-17","email_msg":"","email_subject":"","spoof_name":"2069632789","sms_to":"2062401665","email_your_name":"","sms_msg":"I am going to kill you. I have killed people before and will do it again.","user":"dakman33","id":"32230"},
As this message demonstrates, the service has been used for unethical purposes. In addition, many personal and sensitive messages were included in this dump. According to @ligatthacker, the attack was carried out via SQL injection. This is not the first time Evans has been compromised, and not the first time Evans' has run into SQL injection problems.
A quick processing of the raw data suggests thare are approximately 8,900 unique user IDs. While there were 32,167 messages included in the dump, they appear to have been sent between 2008-06-27 and 2012-03-22. That suggests this data was not taken recently, but rather just leaked today.If this does represent every message ever sent through the service, it calls into question Evans' claim that "since 2007, over 2 million calls have been made using our service." At the time of this article, SPOOFEM.com has not been responding. According to archive.org, the last time a copy was obtained was February 10, 2011. Searching Google for "spoofem.com" does not give the site as the first hit, as is customary, so we cannot verify it has been up recently via Google's cache. The last tweet from @SPOOFEM was done on March 8, 2012. All of this suggests that the data may have been taken shortly before the site / service was shut down.
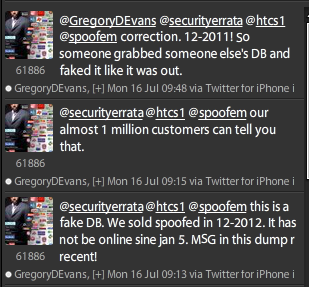
Update #1 (7/16/2012): Greg Evans has replied on Twitter claiming that the database does not belong to Spoofem and is fake (which is it?). He claims that SPOOFEM was sold in December, 2011, and has not been online since January 5, 2012, but fails to note that he and his company were still Tweeting on @SPOOFEM as of March 8, 2012. Evans also failed to note many messages are specific to spoofem.com, disproving his claim that it was not their database:
{"email_to":"rowenrowe@yahoo.com","time":"12:22:29","date":"2010-11-23","email_msg":"Felicia,\r This is Kipp. I am emailing you from the spoofem program...see how an email can be sent from any email address, disguising the author? The free download is available at spoofem.com \r -Kipp-","email_subject":"from Kipp Sutton","spoof_name":"","sms_to":"","email_your_name":"rowenrowe@yahoo.com","sms_msg":"","user":"","id":"15109"},
{"email_to":"","time":"20:04:23","date":"2010-09-28","email_msg":"","email_subject":"","spoof_name":"3174954012","sms_to":"3175865156","email_your_name":"","sms_msg":"hey misty this is sierra. i am using spoofem...does it actually work? does it look like its from erics phone?","user":"sdean14","id":"13096"},
{"email_to":"aj@97bht.com","time":"10:49:59","date":"2009-07-17","email_msg":"Here's your example of SPOOFEM.com! Feel free to contact me at 678-528-4525 to set up an interview with creator Gregory Evans or for additional information. ","email_subject":"SPOOFEM","spoof_name":"","sms_to":"","email_your_name":"BSpears@BritneySpears.com","sms_msg":"","user":"aduggan","id":"2930"},
{"email_to":"Spoofem","time":"07:19:28","date":"2009-06-09","email_msg":"On Friday, 6/5/09, I made 2 separate $9 payments to my Spoofem account. Neither have been applied to my spoofem account, yet the funds have been deducted out of my account. The 2nd payment was made in error, thinking the 1st transaction didnt go through. I had no intentions of purchasing $18 worth of minutes. Please research & either credit me back or apply to my account. Thanks.","email_subject":"No credit for money applied to account","spoof_name":"","sms_to":"","email_your_name":"NastyGirl","sms_msg":"","user":"NastyGirl","id":"2490"},

Update #2 (7/16/2012): @ligatthacker tweeted again today and released a new file (users.json.asc) that appears to contain the full list of users for the SPOOFEM service. Based on that file, there are 57,770 users. The first two lines of the file give a heading and an example user:
{"leak_date":"2012-07-16","total_accounts":57747,"website":"spoofem.com","related_link1":"http://bayfiles.com/file/gOrd/EN6yi0/spoofem.json.asc","related_link2":"http://securityerrata.org/errata/charlatan/gregory_evans/ligatt26/"},
{"done":"No","ip":"108.127.30.90","processed":"No","contact":" <br><br>, <br>valeriesanti@yahoo.com<br>7742694925","last_processed":"0000-00-00 00:00:00","last_error":"","created":"2012-02-05 13:32:45","amount":"1.00","user":"valeriesanti","id":"65489"},